Organizations keep software applications safe, not by chance, but by preparation. Record breaking exploits in 2017 suggest that companies were simply not prepared to govern rising risks -- especially when it came to open source vulnerabilities.
New information publicized this week about a vulnerability (CVE-2017-8046) in the popular Spring component, is bound to test whether software development organisations learned anything from last year’s Struts 2 breach.
The Spring vulnerability, and a related patch, are not new. Both were responsibly, and publicly, disclosed in September 2017 after researchers at LGTM discovered it.
What is new however, is that media stories began appearing on Monday -- more than five months after the fact -- begging the question, just how much did companies learn from last year’s Struts exploit?
The issue is simple. Once public disclosure was made in September -- how many companies were paying close attention with automated tooling and therefore acted quickly to remove the risk from their software supply chains? Conversely, how many companies with manual governance practices failed to even notice the disclosure, and therefore did nothing?
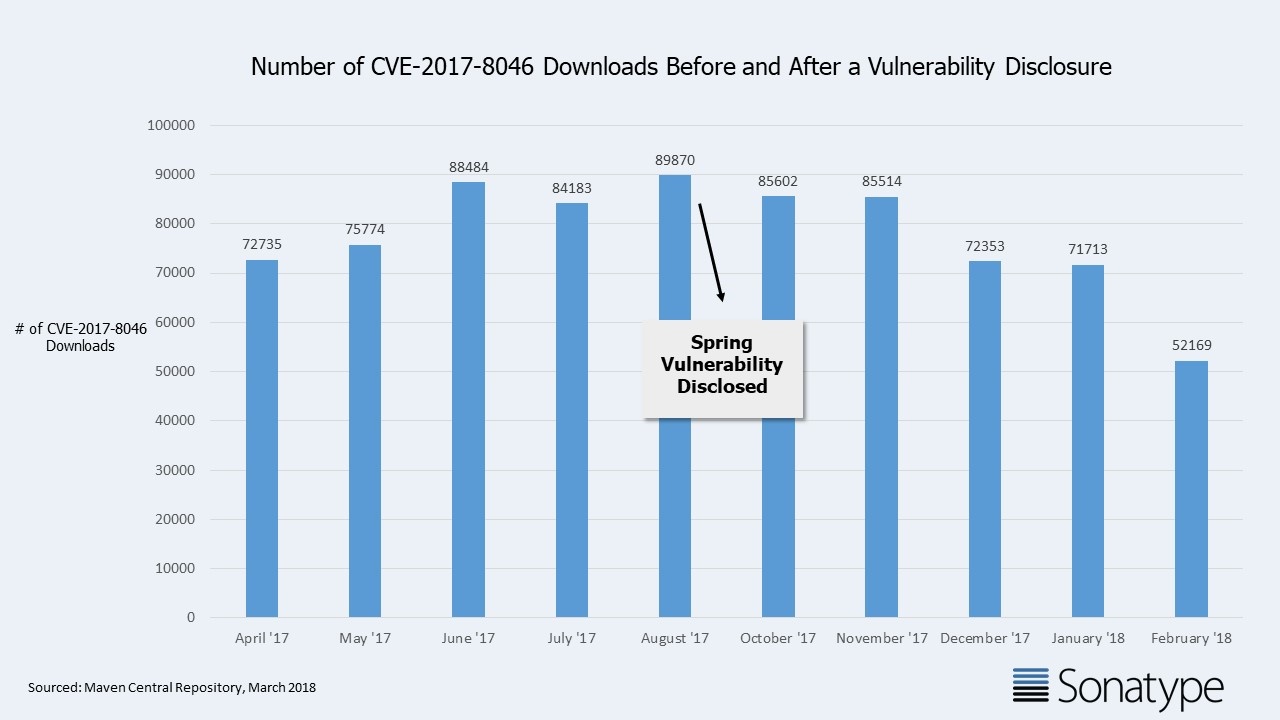
New research from Maven Central, the world’s largest public repository for Java components, reveals the following:
- For the 5 months prior to the September 2017 disclosure, developers downloaded the affected Spring components 411,046 times while they were believed to be good.
- In the 5 months after the September 2017 disclosure, developers downloaded the affected Spring components which were then known to be vulnerable 367,351 times. Only an 11% dip.
An 11% drop in the consumption of these components is typical for any older release, and therefore this represents no measurable change in behavior post CVE disclosure.
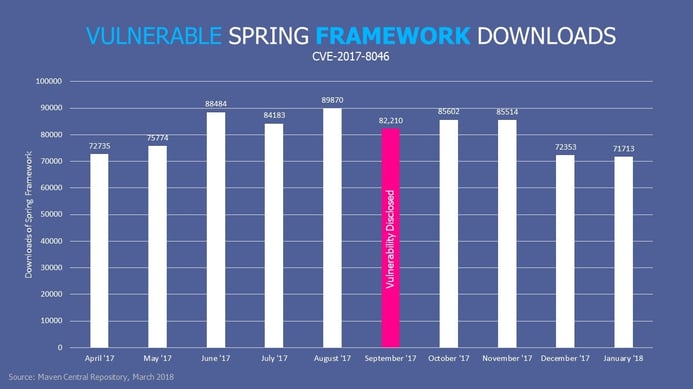
As you can see -- it appears that most companies are learning slowly.
For those unsure if you’re using the vulnerable version of Spring, we offer a free application health check so you can determine exactly which open source components exist within your applications.
.jpg)

