Featured Article
Devs flood npm with 15,000 packages to reward themselves with Tea 'tokens'
By Ax Sharma on
April 16, 2024
vulnerabilities
The Sonatype Security Research team has identified over 15,000 npm packages that flood npm registry in a new trend where devs involved in the blockchain and cryptocurrency communities are leveraging
- Filter by:
- News & Views
- Product
- DevSecOps
- Open Source
- AppSec
- Vulnerabilities
Hear no Evil, See no Evil, Deploy no Evil
By
David Jones on August 20, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
I was going to start off listing a series of what I think are easy questions that I reckon everyone in technology should be able to answer even if they are.
Read More...
Part 3 – [ ________ ] is the Best Policy
By
David Jones on August 18, 2014
open source survey
3 minute read time
In part 1 and part 2 of the '[ ________ ] is the Best Policy' series, we looked at how open source policies can quite often lead to the wrong type of behavior.
Read More...
"Wait! Wait! Don't pwn me!" from Black Hat 2014
By
Mark Miller on August 14, 2014
OWASP
1 minute read time
"Wait! Wait! Don't pwn me!" from Black Hat 2014
Read More...
Part 2 - [ ________ ] is the Best Policy
By
David Jones on August 13, 2014
open source survey
3 minute read time
In Part 1, ‘[ ________ ] is the Best Policy, we looked at some of the common aspects of an open source policy and discussed how our recent survey discovered.
Read More...
Part 1 - [ ________ ] is the Best Policy
By
David Jones on August 11, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
Open source has been around for donkey's years but until recently the persuasive argument of “many eyeballs” was the guiding policy using open source.
Read More...
Two AppSec Questions Always Asked
By
Brian Fox on July 24, 2014
Cyber Supply Chain Management and Transparency Act
4 minute read time
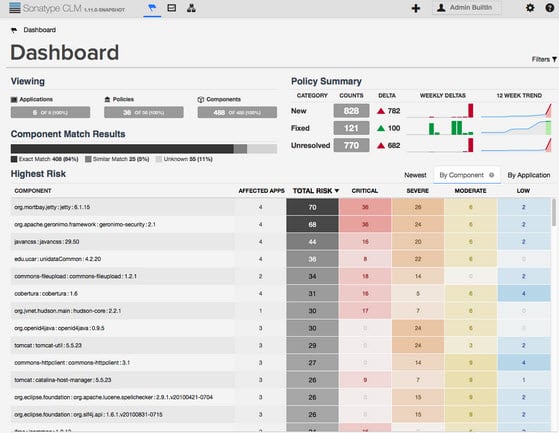
While Repository Health Checks are valuable, we just released something even better: the CLM 1.11 Dashboard.
Read More...
Part 2: The Internet of Everything: Code, Cars, and More
By
Wayne Jackson on July 24, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
In part one of my blog, It's Just the Way Software is Made, I discussed the realities of how software is made, the birth of agile development, and the.
Read More...
Trusting Third-Party Code That Can't Be Trusted
By
Derek Weeks on July 22, 2014
Component Lifecycle Management
2 minute read time
Paul Roberts (@paulfroberts) at InfoWorld recently shared his perspective on “5 big security mistakes coders make”.
Read More...
Part 3: The Internet of Everything: Code, Cars, and More
By
Wayne Jackson on July 21, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
In part two of my blog 'A Closer Look at Today's Software Supply Chain', I discussed why human-speed supply chain management can’t keep pace with today’s.
Read More...