Featured Article
Devs flood npm with 15,000 packages to reward themselves with Tea 'tokens'
By Ax Sharma on
April 16, 2024
vulnerabilities
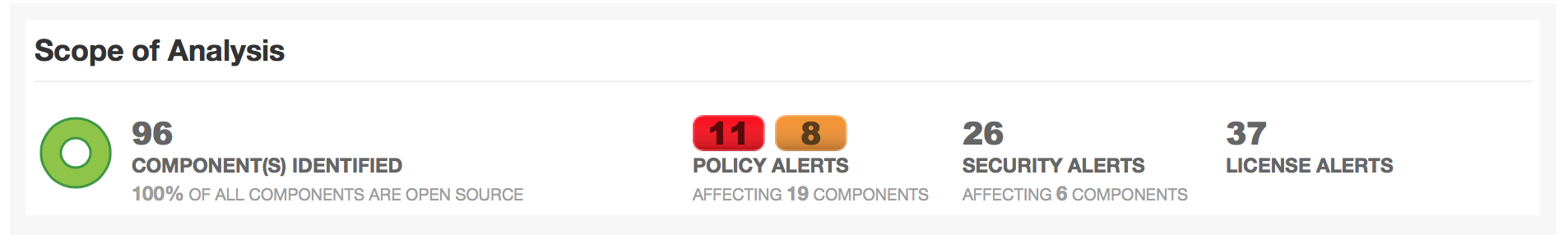
The Sonatype Security Research team has identified over 15,000 npm packages that flood npm registry in a new trend where devs involved in the blockchain and cryptocurrency communities are leveraging
- Filter by:
- News & Views
- Product
- DevSecOps
- Open Source
- AppSec
- Vulnerabilities
How a Software Bill of Materials Uncovers Known Vulnerabilities
By
Derek Weeks on April 30, 2015
Cyber Supply Chain Management and Transparency Act
3 minute read time
How a Software Bill of Materials Uncovers Known Vulnerabilities
Read More...
Talking Turkey in Texas: Open Source Governance Lags
By
Derek Weeks on November 25, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
Talking Turkey in Texas: Open Source Governance Lags
Read More...
CIO.com: Helping Developers Reduce Open Source Risk
By
Derek Weeks on November 17, 2014
Cyber Supply Chain Management and Transparency Act
1 minute read time
CIO.com: Helping Developers Reduce Open Source Risk
Read More...
Bash 2014 - This Is Not a Party
By
Derek Weeks on September 25, 2014
Cyber Supply Chain Management and Transparency Act
2 minute read time
I can honestly say that although referred to by the media as Shellshocked, I am neither shocked nor awed.
Read More...
Skeleton Key
By
Derek Weeks on September 19, 2014
Cyber Supply Chain Management and Transparency Act
2 minute read time
A skeleton key is capable of opening any lock regardless of make or type. Do you know anyone who has one? I do. Lots of them.
Read More...
Time for Full Open Source Disclosure
By
Derek Weeks on September 12, 2014
Cyber Supply Chain Management and Transparency Act
4 minute read time
We are not the first industry to face this challenge. But many are convinced our problem is much smaller than it really is or that it does not exist.
Read More...
Part 2: The Internet of Everything: Code, Cars, and More
By
Wayne Jackson on July 24, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
In part one of my blog, It's Just the Way Software is Made, I discussed the realities of how software is made, the birth of agile development, and the.
Read More...