Featured Article
Devs flood npm with 15,000 packages to reward themselves with Tea 'tokens'
By Ax Sharma on
April 16, 2024
vulnerabilities
The Sonatype Security Research team has identified over 15,000 npm packages that flood npm registry in a new trend where devs involved in the blockchain and cryptocurrency communities are leveraging
- Filter by:
- News & Views
- Product
- DevSecOps
- Open Source
- AppSec
- Vulnerabilities
Your Guide to AppSec Tools: SAST or SCA?
By
Alyssa Shames on April 16, 2020
AppSec
4 minute read time
Software composition analysis speeds time to innovation by automating manual open source governance processes that are prone to errors.
Read More...
Why Software Composition Analysis (SCA) Demands Precision
By
Katie McCaskey on July 24, 2019
Software composition analysis
3 minute read time
Software Composition Analysis: Getting to the Signal Through the Noise, by 451 Research, demonstrates Sonatype's leadership in software composition analysis.
Read More...
Software Composition Analysis: A Matter of Perspective (and Experience)
By
Wayne Jackson on April 08, 2019
Software composition analysis
2 minute read time
The SCA market is young - leaving everyone wrestling with a critical question: is it a security-centric, developer-centric, or a legal-centric endeavor? At.
Read More...
Software Composition Analysis: Precision Definitely Matters (Just Ask Our Competitors)
By
Matt Howard on July 24, 2018
Software composition analysis
3 minute read time
Just two years ago, SCA was more about helping traditional security professionals identify suspects across a broad spectrum of open source ecosystems.
Read More...
Malicious Intent: Open Source Developers, Please Protect Your Users
By
Brian Fox on February 14, 2018
software bill of materials
1 minute read time
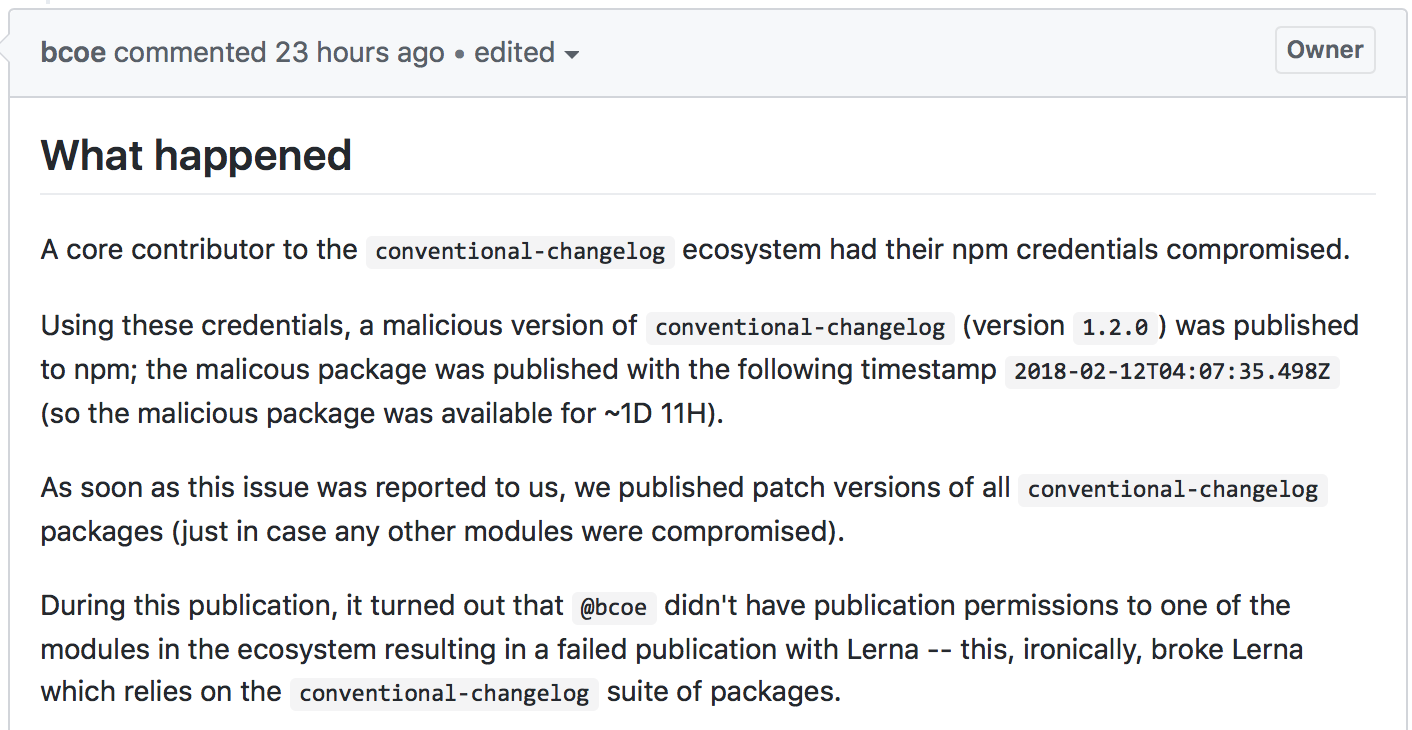
Pay attention to your own digital security as you would if you were protecting millions of others. Malicious code found in npm package conventional-changelog.
Read More...
The Hijacking of a Known GitHub ID: go-bindata
By
Brian Fox on February 07, 2018
Software Supply Chain
2 minute read time
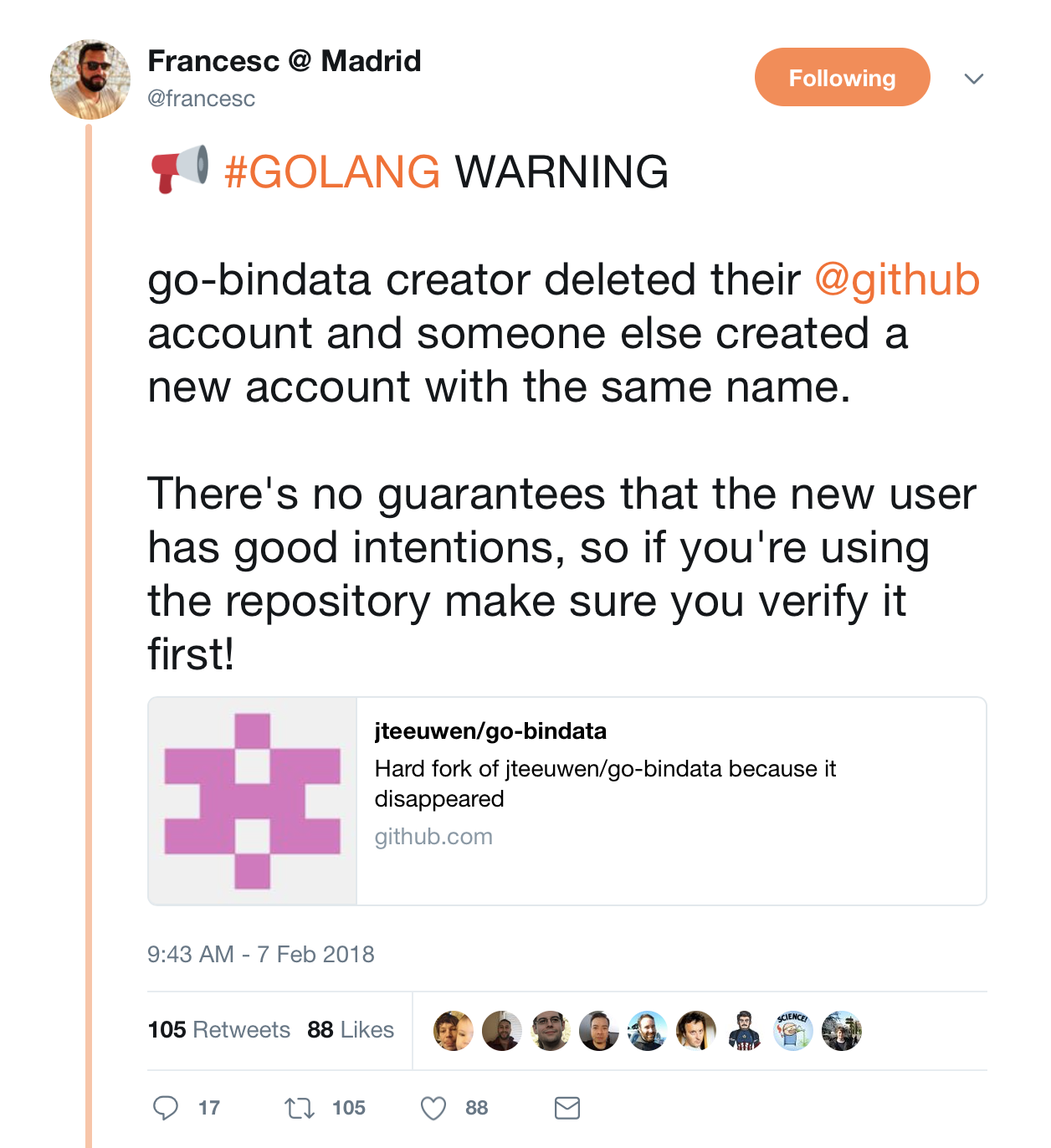
the creator of go-bindata deleted their @github account and someone else created a new account under the same name
Read More...
Better data improves mean times to repair in DevSecOps pipelines.
Read More...
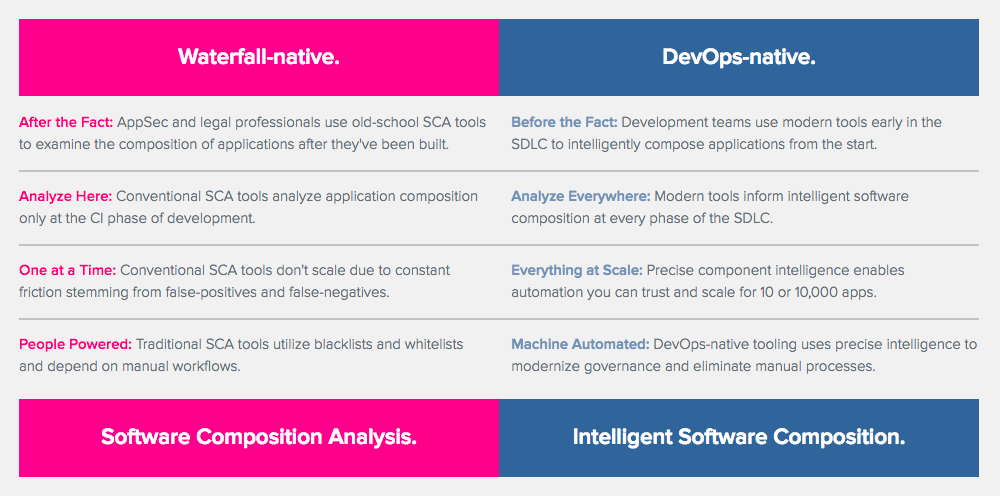
How DevOps Killed the Market for Software Composition Analysis
By
Matt Howard on February 28, 2017
Application Security
1 minute read time
SCA tools are waterfall-native by design. It is impossible to integrate SCA security controls into DevOps-native work flows in an automated and scalable way.
Read More...