Meet npmjs.com, a video and eBook hosting platform — not our words, but it seems that's what goes in the mind of some users (and attackers) recently seen misusing the platform to store media like multi-gig movies, videos, and eBooks.
Today, the Sonatype Security Research team came across 748 packages flooding the npm registry. Contrary to containing malware though, these tell a different story...
Who needs YouTube?
Video hosting for Devs
In recent times, users of software development repositories like npm, PyPI, and GitHub have found unique use cases that technically deviate from the core purpose that these platforms were designed for — to store software artifacts.
Repos and packages published to these services have frequently featured anything from malicious code, to malware research samples, to media like movies, films and eBooks. While multimedia assets can certainly be and are often an integral aspect of legitimate software apps, the 748 packages caught today and being purged from the npm registry in real time contain movies, split into partial video clips.
Tracked as sonatype-2024-0284, each of these packages is roughly 54.5 MB in size and named with a 'wlwz' prefix followed by a set of numbers, perhaps to denote a sequence in which these should be downloaded and processed to reconstruct the entire movie contained in them. Timestamps show that these packages have been sitting on the npm registry since at least December 4, 2023, but GitHub began removing them from the npmjs.com registry this week.
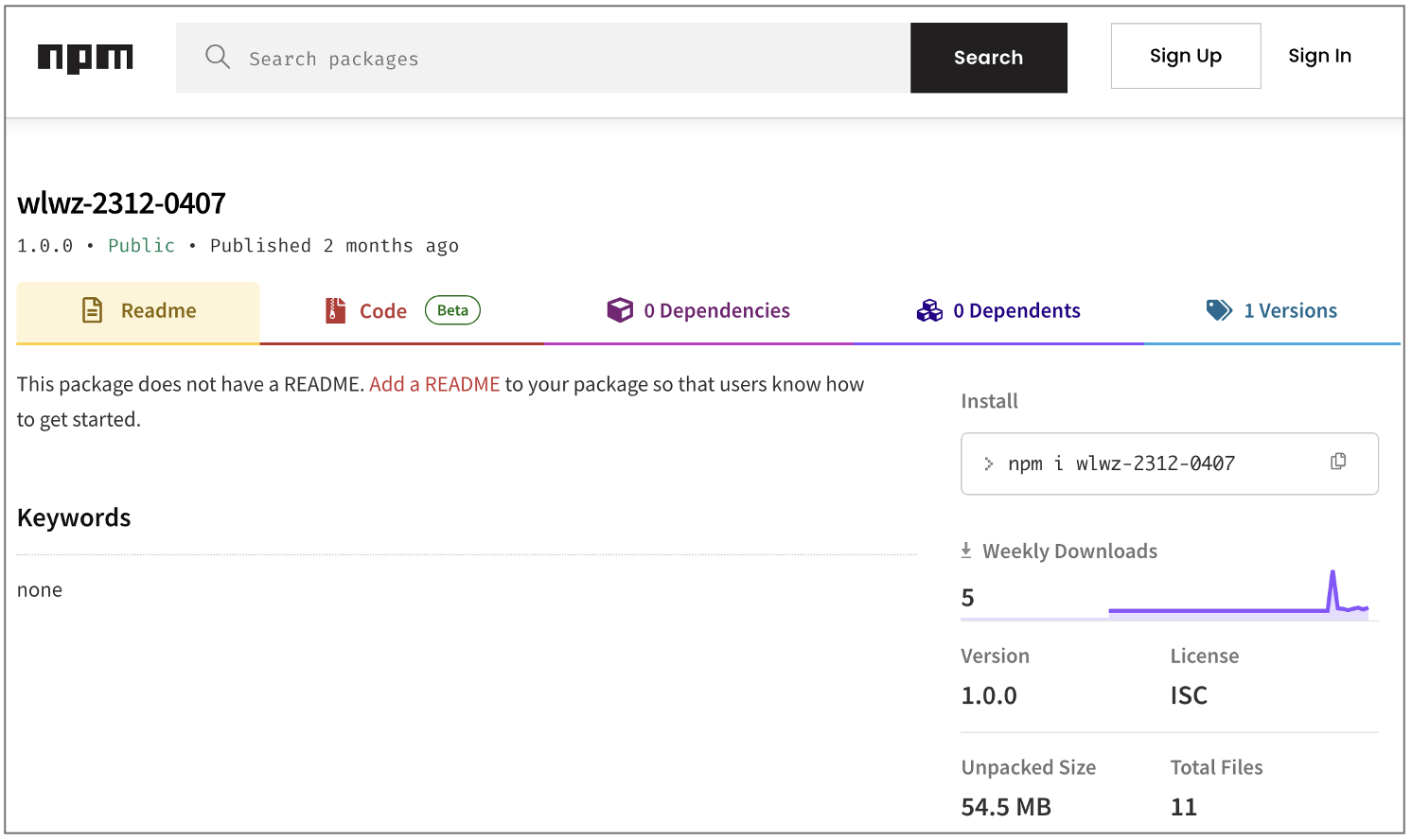
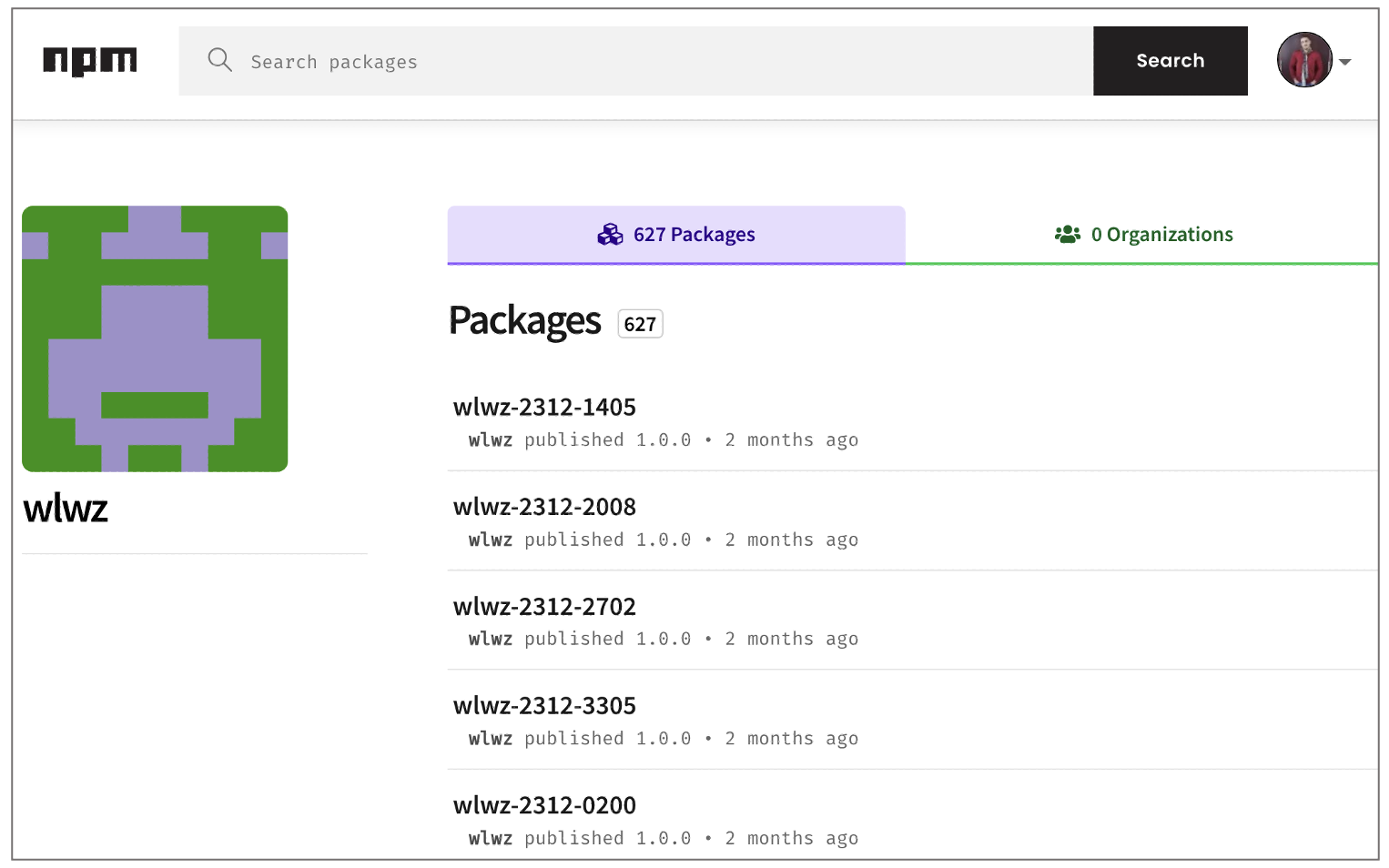
The npm user behind these artifacts is called wlwz, by the very prefix contained in the name of these packages.
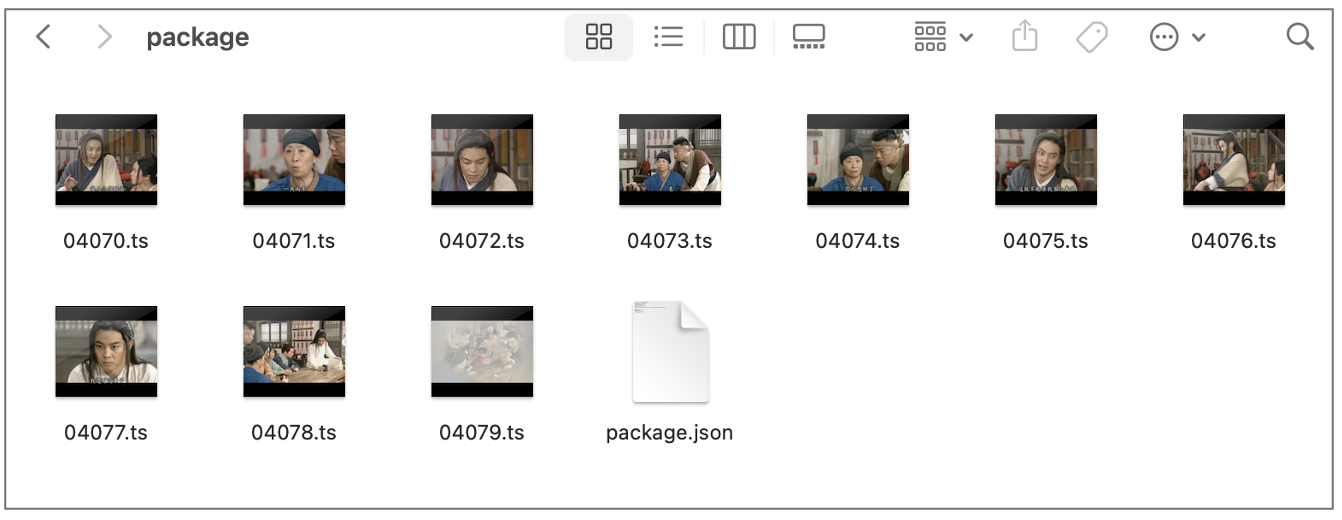
Within each package are video clips ending in the '.ts' extension, which indicates these were ripped from DVDs and Blu-ray discs. (The '.ts' extension, in this context, is not to be confused with TypeScript).
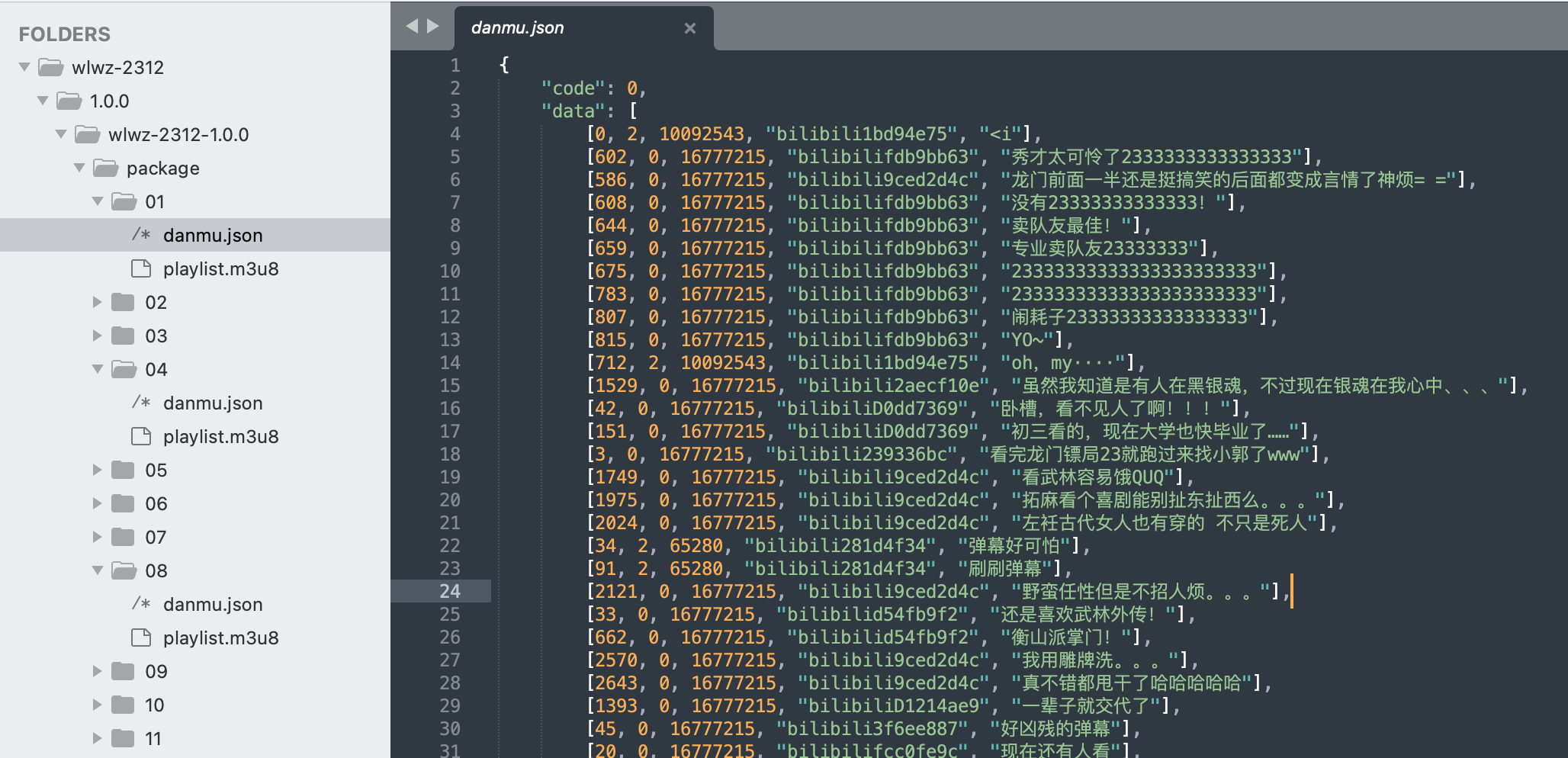
As for the titles of movie clips in question, we are not certain, but some packages, like "wlwz-2312" contain timestamped Mandarin comments* in JSON files.
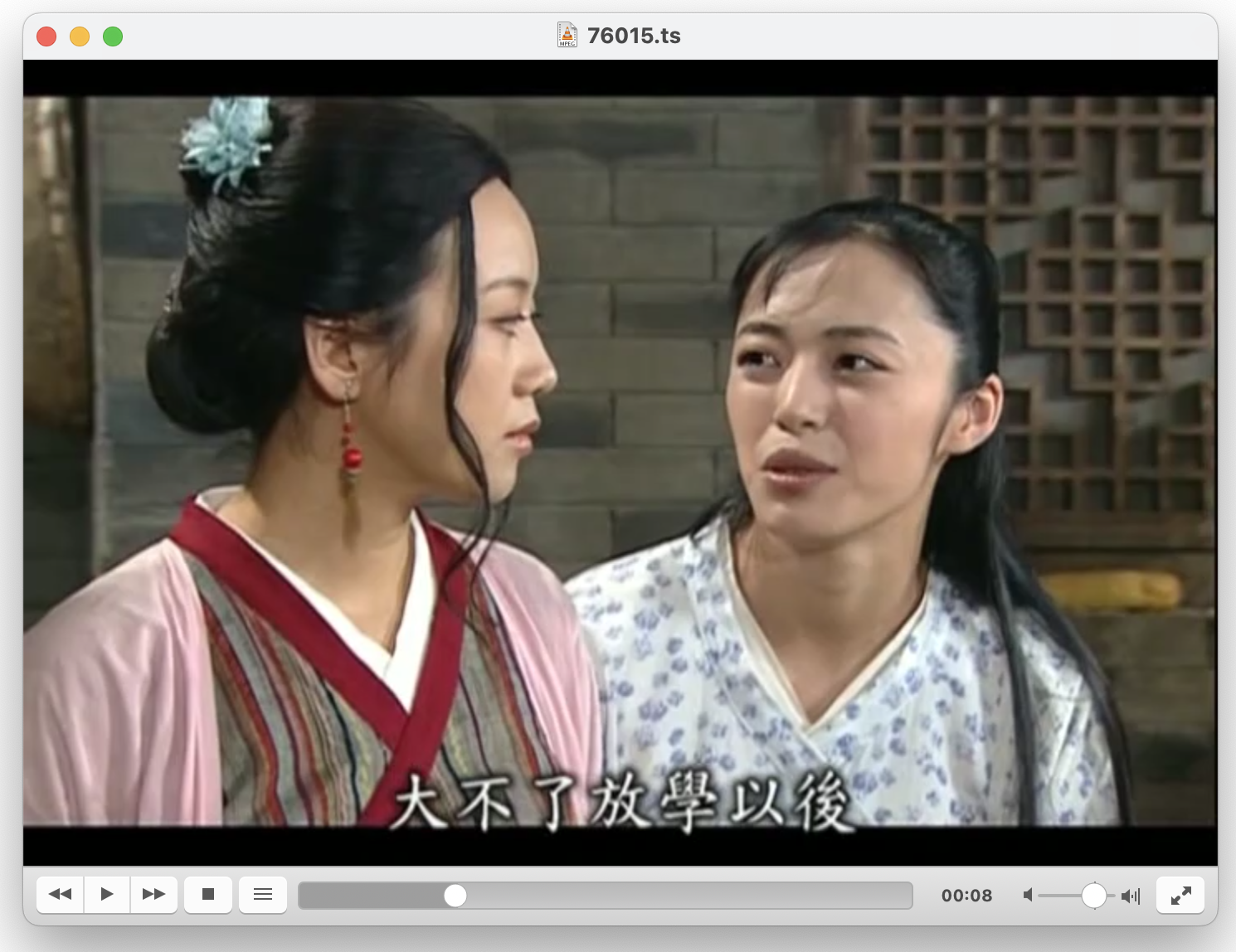
...which compels me to say, the incident has echoes of 2022, when Chinese devs were seen (ab)using GitHub and npm to store 1000s of eBooks, possibly as a means to circumvent state censorship. Although, it's entirely possible that this is a sheer abuse of the registry for hosting pirated materials.
While we have frequently identified and reported on events where open source registries were flooded with hundreds of cryptominers, spam packages, and dependency confusion malware, incidents like these illustrate the innovate ways in which users (and attackers) are using such registries and how their seemingly benign actions can ultimately threaten the integrity and hygiene of these platforms, and the overall software supply chain.
In conclusion, don't upload videos to OSS registries: at a minimum you are most certainly violating their terms of service!
*Update, Feb 2nd, 2024: A prior version of this article implied that the JSON file(s) in question contain subtitles, but thanks to the feedback from a reader, it turns out, the JSON contents represent time-synced user comments submitted to online video streaming platforms. We have since updated the article.
Repository Firewall customers remain safe
Sonatype's products such as Repository Firewall and Lifecycle stay on top of nascent attacks and vulnerabilities and provide you with detailed insights to thwart malware, Potentially Unwanted Applications (PUAs), and vulnerable components from reaching your builds:
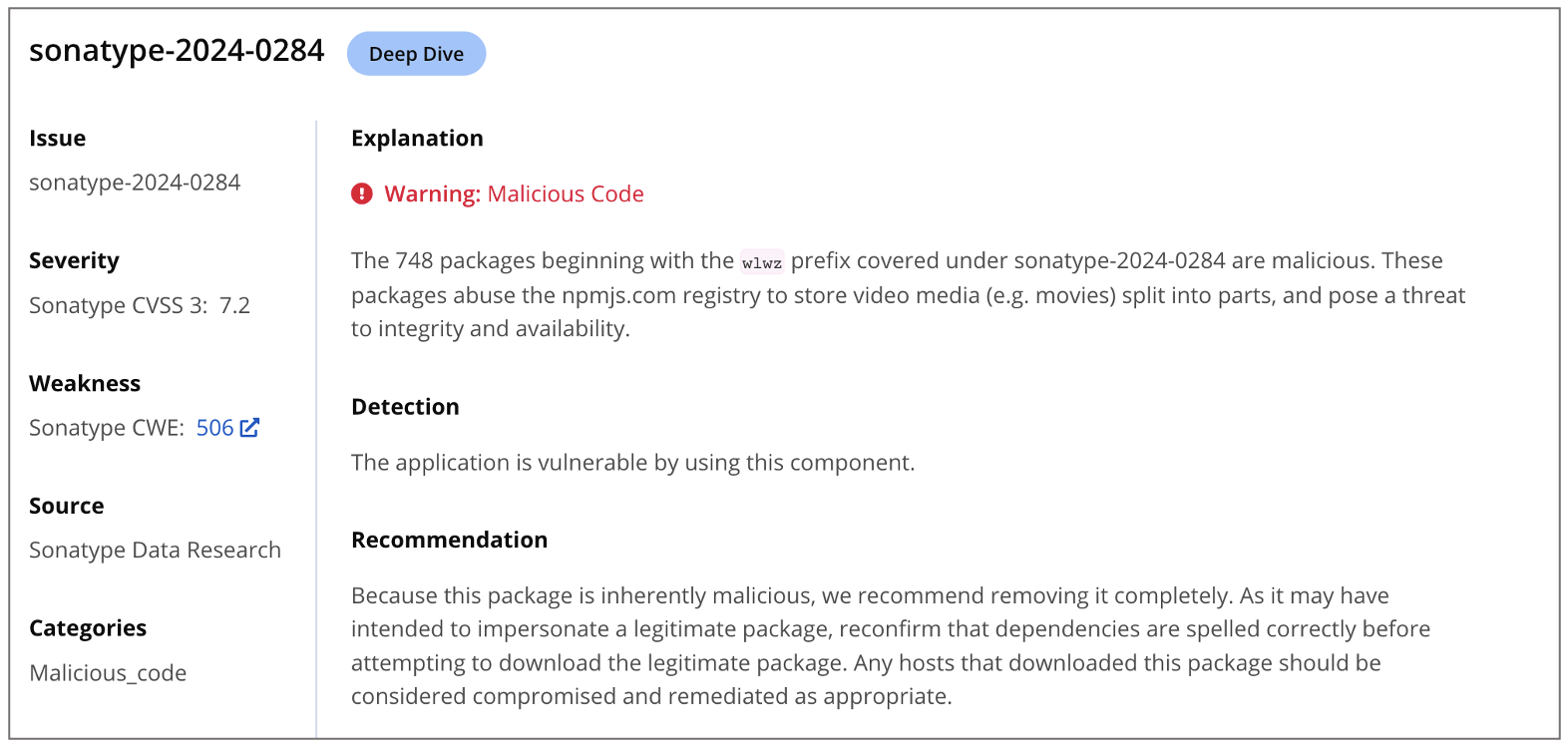
Users of Sonatype Repository Firewall can rest easy knowing that these packages would automatically be blocked from reaching their development builds and keep their software development life cycle (SDLC) hygienic.






